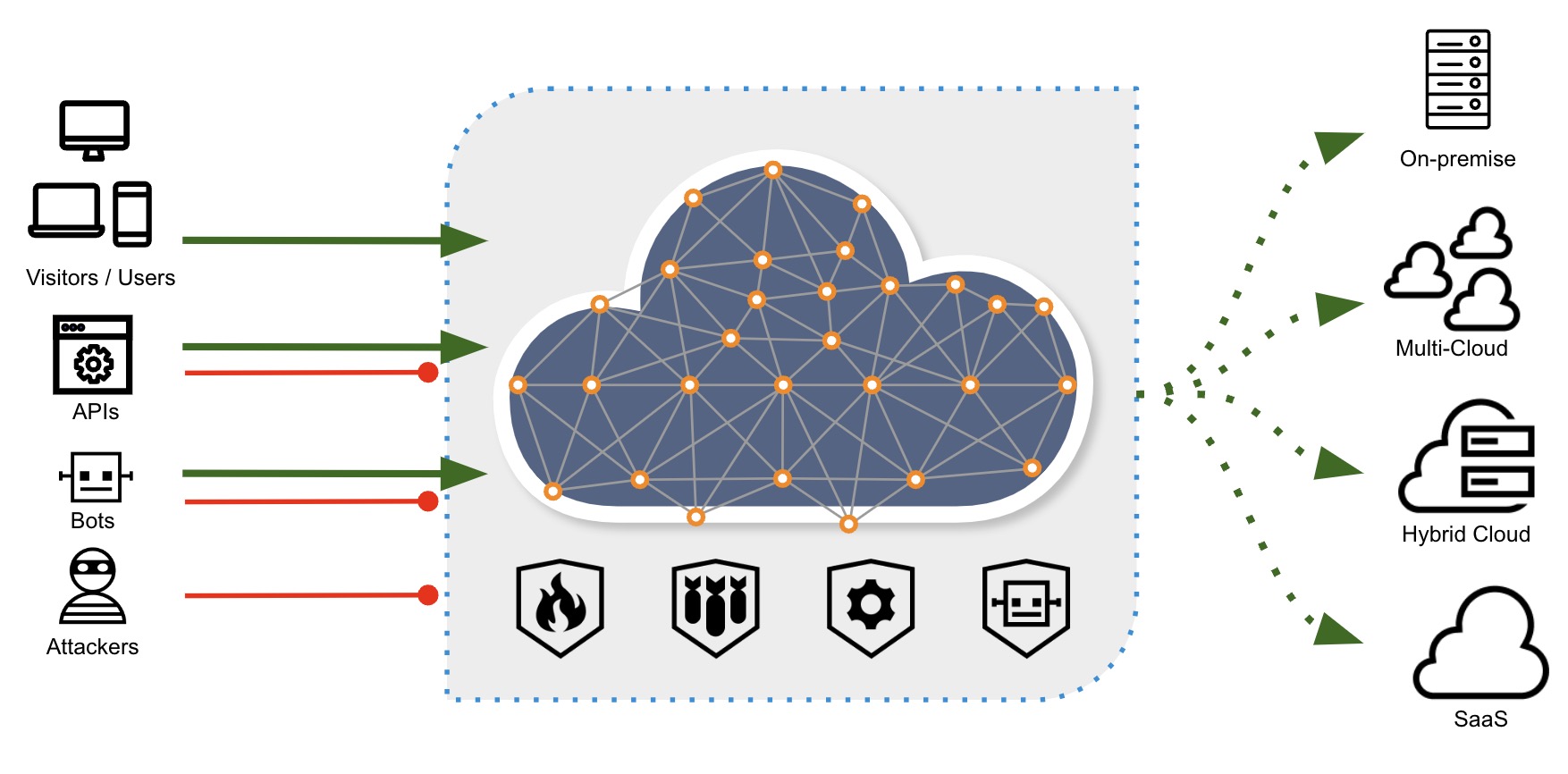
Apps and APIs - Protect your brand by securing apps and APIs from persistent threats

IaaS Linode Region - Osaka, Chicago
EAA Portal https://partnerdemo.login.go.akamai-access.com If you don't have login credential, please reach out your regional Partner SE. Web Server https://www.akamaidmeo.xyz If you don't have login credential, please reach out your regional Partner SE.
Here is the Attack Script Example available. If your access is not allowed please contact your relevant Partner SE of Akamai
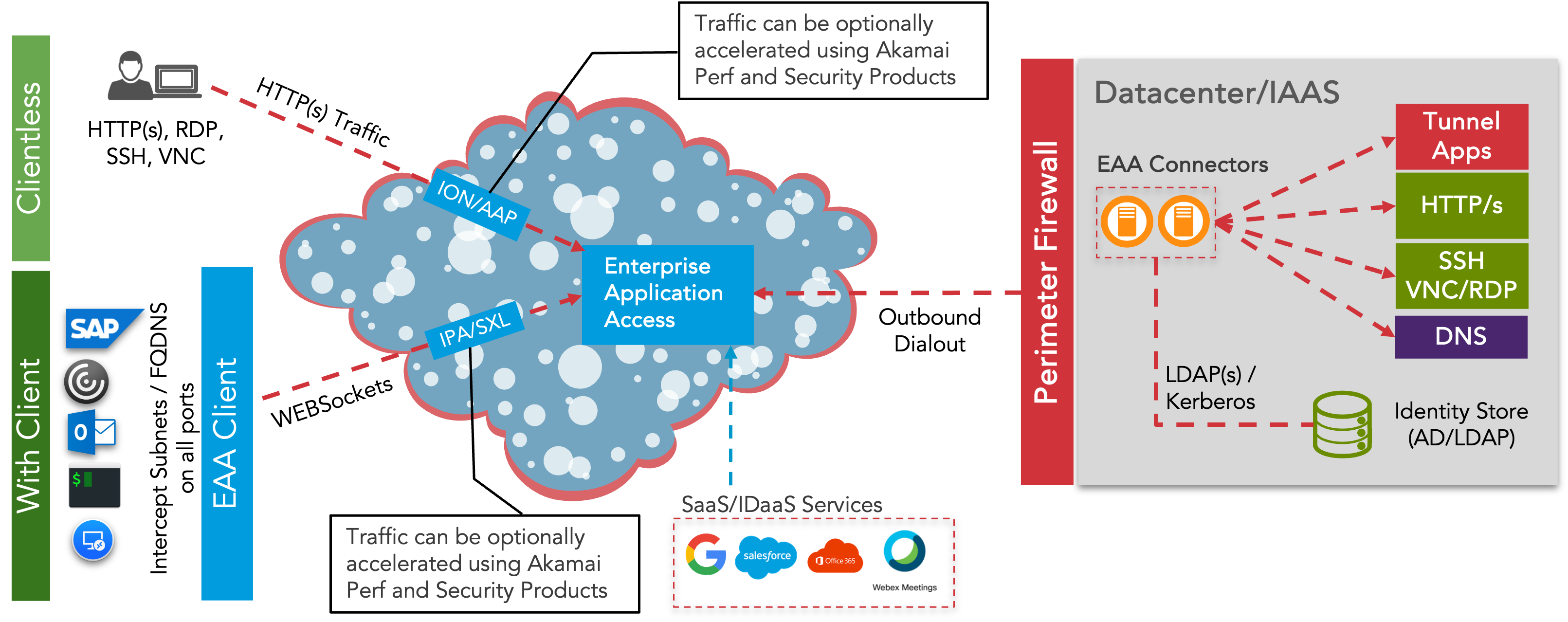
Data Edge Provides the data plane between the user and the application, as well as the data security, application performance and optimization components. Management edge Provides management, logging, reporting, and configuration capabilities. The Enterprise Application Access management and data edges are based on a secure, multi-tenant architecture or a dedicated single-tenant data cloud. Enterprise connector See connectors. Connectors communicate with your applications (usually on a private subnet) and with the the Enterprise Application Access Cloud (through outbound TLS sessions on port 443) to connect your authorized users with the applications.
IP/Geo Firewall Block or allow access based on a requestor's IP address or geographic location Dos Protection Keep your site safe from overwhelming traffic. Our web application firewall is deployed across the Akamai Intelligent Platform, so attacks are blocked far from your origin server, at the edge of Akamai’s network. Sophisticated controls can thwart data flood and slow POST attacks. Rate limits let you flag request traffic that’s too fast to be from a human. Client Repputation Stop malicious clients before they can attack, based on Akamai’s visibility into prior behavior of individual IP addresses. Billions of IP addresses interact with the Akamai platform every month. Based on that intelligence, Client Reputation calculates the likelihood that an IP address may fall into a malicious category like: web attacker, denial of service (DoS) attacker, scanning tool, or web scraper. Available with App & API Protector with Advanced Security Management Web Application Firewall Our latest web application firewall protection engine delivers advances that help you protect your websites and APIs with less effort and greater accuracy. Bot Management Your website lets many entities interact with you online, including partners, competitors, attackers, and fraudsters using automated bots. Some bots are positive, like Google search crawlers. Others may not be. How you handle bots, depends upon your needs: - To see what bots are hitting your site and then mitigate or allow them, you can use the bot protections that come included with App & API Protector. This offering is called Bot Visibility and Management. - You may have specific transactional endpoints you need to protect. For example, credential stuffing bots are attacking your login page. To stop attacks like this and combat sophisticated bots, turn to Bot Manager Premier, which you can add on to App & API Protector.
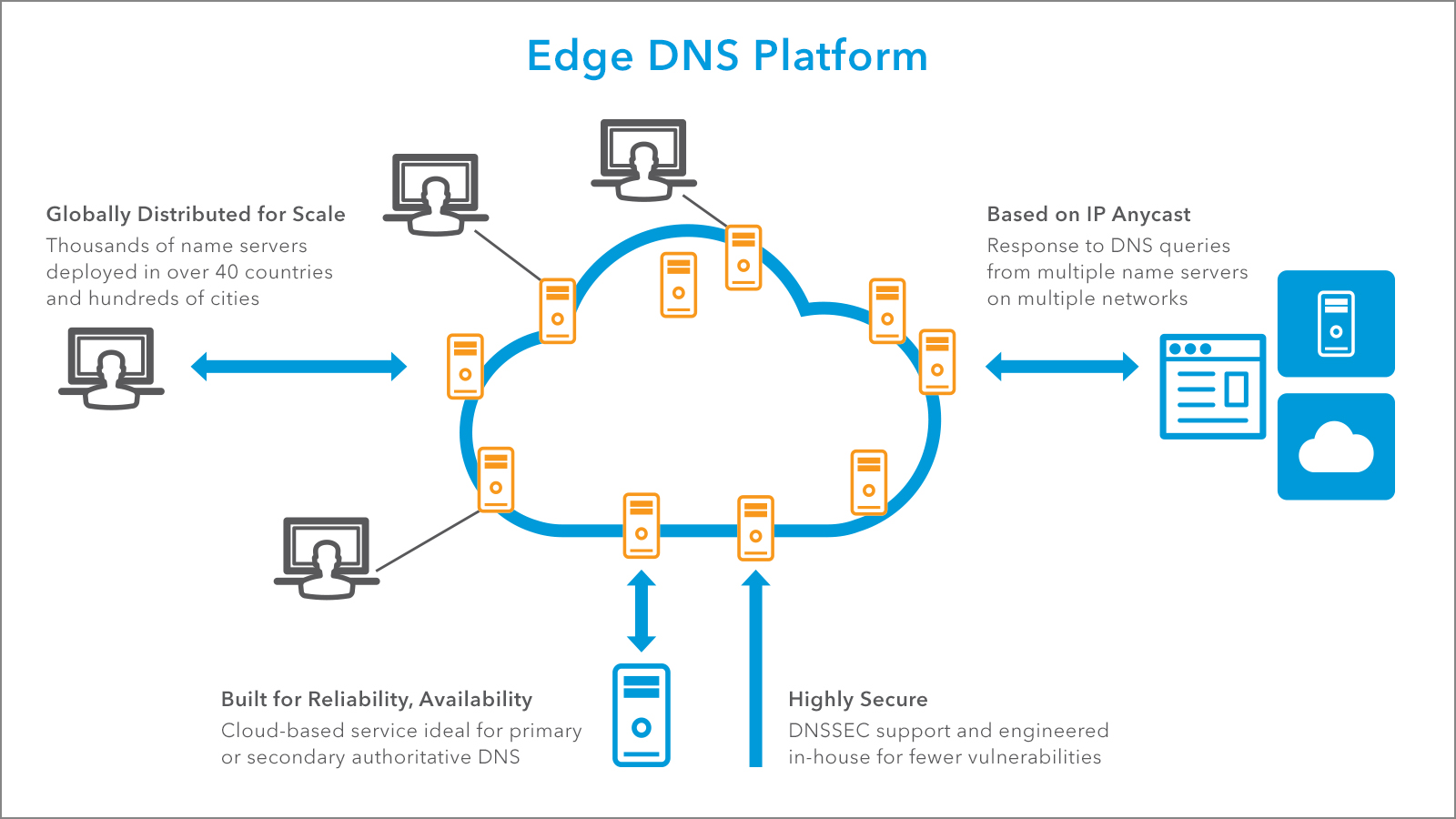
Edge DNS is an authoritative DNS service. It provides a secure, high-performance, scalable, and highly available edge service for authoritative DNS. Edge DNS uses Akamai's global deployment of thousands of name servers across multiple networks, uses IP Anycast, and relies on a proprietary implementation of the DNS protocol as a common component of the Akamai Intelligent Platform. Edge DNS complements existing web infrastructures, whether deployed in a private data center or public cloud, connecting users with their desired destination.
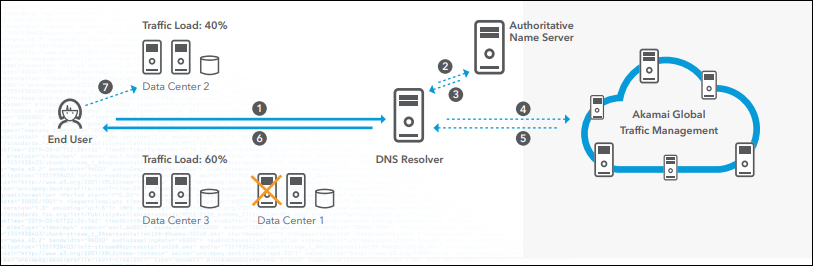
Global Traffic Management (GTM) is a cloud-based intelligent traffic manager that supports business continuity and your growing user base and uses load balancing to manage website and mobile performance demands. GTM helps Internet users access your website or IP applications with greater reliability. It applies an Internet-centric approach to global load balancing to increase site availability and responsiveness to online user requests. Unlike traditional hardware-based solutions that reside within data centers, the fault-tolerant GTM service makes intelligent routing decisions. These are based on real-time data center performance health and on global Internet conditions. They transport user requests to the appropriate data center based on the best Internet route for that user at that moment. In this document, the term end user represents those who generate the traffic that the site administrators, project managers, and technical support providers are using GTM to manage. The term you refers to site administrators, project managers, and technical support providers, the roles most commonly responsible for managing GTM.
GTM is designed so that Internet users can more reliably get to your websites or any other IP application. It applies an Internet-centric approach to global load balancing to provide high site availability and responsiveness to online user requests. Unlike traditional hardware-based solutions that reside within the data center, Akamai’s GTM service is a fault-tolerant solution that makes intelligent routing decisions based on real-time data center performance health and global Internet conditions, routing user requests to the most appropriate data center using an optimized route for that user at that moment.